Overview of the ISC2 CISSP Exam
The ISC2 CISSP certification is widely regarded as the gold standard in information security certifications. Designed for experienced security practitioners, the CISSP validates deep technical and managerial knowledge across eight domains of the (ISC)² CISSP Common Body of Knowledge (CBK), including Security and Risk Management, Identity and Access Management (IAM), Security Architecture and Engineering, and more.
One of the core topics covered in the exam—and critical to real-world security management—is authentication in network security. Understanding how authentication mechanisms work, their implementation, and the underlying technologies is vital for any CISSP candidate aiming to protect digital assets from unauthorized access.
At DumpsBoss, we provide up-to-date CISSP exam dumps and study resources that delve into these core areas, helping you get certified faster and more confidently.
Definition of Authentication in Network Security
Authentication in network security refers to the process of verifying the identity of a user, device, or system before granting access to networked resources. It ensures that individuals or entities requesting access are who they claim to be. Unlike authorization, which determines what an authenticated entity can access, authentication is all about proving identity.
For instance, when you log into your corporate VPN with a username and password, you’re undergoing authentication. If you're prompted for a fingerprint or a code from your mobile device, you’re using multi-factor authentication, a stronger and more secure method.
Purpose of Authentication in Network Security
1. Ensures Authorized Access
The primary goal of authentication is to restrict access to authorized users only. In environments where sensitive data is stored—such as financial records, intellectual property, or personal information, unauthorized access can lead to disastrous consequences. Authentication acts as the first line of defense by allowing only verified users to enter the system.
2. Protects Confidentiality
Confidentiality refers to ensuring that data is not accessed by unauthorized individuals. Authentication plays a crucial role in protecting confidentiality by ensuring that only intended recipients or users can view or interact with sensitive data.
3. Integrity Assurance
By authenticating users and devices, network systems can maintain the integrity of data. Ensuring that only trusted sources can access and manipulate data reduces the risk of tampering or malicious alterations.
4. Prevents Identity Theft and Fraud
Authentication protocols are designed to detect spoofing or impersonation attempts. By requiring verifiable credentials, systems can prevent cybercriminals from posing as legitimate users, thus thwarting identity theft, phishing attacks, and other fraud tactics.
5. Enhances Compliance
Organizations across industries must comply with data protection laws and frameworks like GDPR, HIPAA, PCI-DSS, and ISO 27001. Strong authentication measures demonstrate compliance with these regulations, protecting both users and enterprises from legal and financial penalties.
Types of Authentication Methods in Network Security
To secure networks effectively, various authentication methods are used. Each has its pros and cons, and in many cases, they're combined to form multi-layered defenses.
1. Something You Know (Knowledge-based)
This is the most basic form of authentication—passwords, PINs, and answers to security questions. Though widely used, knowledge-based methods are vulnerable to brute-force attacks, phishing, and social engineering if not properly managed.
2. Something You Have (Possession-based)
This method requires a user to possess a physical device such as a smart card, USB token, or a mobile phone used for one-time passwords (OTPs). It adds a layer of security but also depends on the security of the device itself.
3. Something You Are (Biometric-based)
Biometric authentication uses unique biological characteristics—such as fingerprints, facial recognition, retina scans, or voice recognition—to verify identity. Biometric methods are increasingly popular due to their uniqueness and resistance to replication.
4. Something You Do (Behavioral-based)
Behavioral authentication analyzes patterns such as typing speed, navigation habits, or usage behavior. It's often used in conjunction with other forms of authentication and is gaining traction with AI-enhanced security systems.
5. Multi-Factor Authentication (MFA)
MFA combines two or more authentication methods—e.g., password + OTP or fingerprint + security token—to create a robust authentication mechanism. It significantly enhances security and is highly recommended by cybersecurity experts and regulators.
DumpsBoss offers scenario-based CISSP practice questions that test your understanding of MFA and its real-world applications, ensuring you're well-prepared for exam success.
Authentication Protocols and Technologies
Understanding the tools and technologies that power authentication is key to implementing effective security. Below are the core protocols every CISSP candidate should know:
1. Kerberos
Kerberos is a secure method for authenticating a request for a service in a computer network. It uses tickets and a Key Distribution Center (KDC) to validate identity without transmitting passwords over the network. Common in enterprise environments, especially those using Windows Active Directory.
2. RADIUS (Remote Authentication Dial-In User Service)
RADIUS is widely used for centralized authentication, authorization, and accounting (AAA). It is especially useful in VPNs and wireless networks, supporting secure transmission of credentials and logging of user access.
3. LDAP (Lightweight Directory Access Protocol)
LDAP is used to access and maintain distributed directory information services. It's frequently used in conjunction with Active Directory for centralized identity management and authentication within enterprise networks.
4. SAML (Security Assertion Markup Language)
SAML is an XML-based framework for exchanging authentication and authorization data between parties. Commonly used in Single Sign-On (SSO) scenarios, especially in web applications and federated identity environments.
Tip: CISSP exam questions often involve comparing these protocols and selecting the most appropriate one based on a scenario. DumpsBoss CISSP dumps include such case-based questions to sharpen your decision-making skills.
Benefits of Network Security Authentication
1. Improved Network Access Control
Authentication is foundational to network access control (NAC), ensuring that only verified users and devices can connect. This minimizes the risk of rogue devices or malicious users accessing the system.
2. Stronger Defense Against Attacks
When combined with encryption and intrusion detection, authentication fortifies the network against phishing, man-in-the-middle (MITM), and brute-force attacks.
3. Increased Accountability and Auditability
Every authenticated user’s actions can be tracked and logged, providing a clear audit trail. This not only supports forensic investigations but also helps in compliance reporting.
4. Protection Against Insider Threats
Authentication doesn't just stop external threats. By enforcing role-based access control (RBAC) and multi-layer verification, it limits what authenticated users can do, reducing risks from insider threats.
5. Scalability and Flexibility
Modern authentication systems are highly scalable and integrate with cloud services, mobile platforms, and legacy systems. Organizations can adapt their authentication strategies as they grow.
Real-World Examples of Authentication in Network Security
Example 1: Enterprise VPN Access
In a large corporation, employees accessing the corporate VPN are required to enter their username, password, and an OTP sent to their registered device. This is a classic multi-factor authentication setup, ensuring security even if a password is compromised.
Example 2: Banking Apps
Modern banking apps use a mix of fingerprint recognition, OTPs, and behavior-based algorithms to ensure users are legitimate. Any deviation in typing pattern or geolocation may trigger additional authentication challenges.
Example 3: Cloud-Based SSO
Companies using cloud apps like Microsoft 365, Salesforce, or AWS often implement SAML-based Single Sign-On, allowing users to log in once and access multiple apps without repeated authentication, streamlining access while maintaining security.
Example 4: Healthcare Systems
In healthcare, where patient data must be fiercely protected, authentication systems use smart cards and biometric scans to ensure that only certified practitioners can access sensitive records, fulfilling HIPAA compliance mandates.
Conclusion
In the world of cybersecurity, authentication serves as the first and most critical defense against unauthorized access and data breaches. Whether you’re a security professional or an aspiring CISSP, understanding authentication methods, protocols, and technologies is non-negotiable.
With evolving threats, robust authentication ensures confidentiality, integrity, and availability—principles at the heart of the CISSP certification. If you're preparing for the ISC2 CISSP exam, solidifying your knowledge of authentication will not only help you pass the test but also prepare you to secure enterprise environments in real life.
DumpsBoss offers expertly curated CISSP dumps, updated questions, and scenario-based practice sets to help you master topics like network security authentication with confidence. Don’t just study harder—study smarter with DumpsBoss, your trusted partner on the path to cybersecurity excellence.
Special Discount: Offer Valid For Limited Time “ISC2 CISSP Dumps” Order Now!
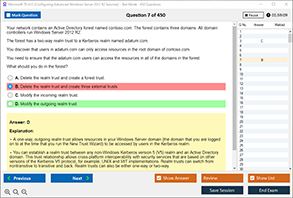
Sample Questions for ISC2 CISSP Exam Dumps
Actual exam question from ISC2 CISSP Exam.
What is the purpose of the network security authentication function?
A) To encrypt data during transmission
B) To verify the identity of users or devices on a network
C) To detect and prevent unauthorized access
D) To monitor network traffic for suspicious activity