Overview of the CompTIA SY0-701 Exam and Combating Piracy with Cybersecurity Techniques
The CompTIA SY0-701 exam is the latest iteration of the CompTIA Security+ certification, a globally recognized credential that validates foundational skills in cybersecurity. Designed for IT professionals aiming to launch or elevate their careers, this exam ensures proficiency in identifying and managing security risks, handling threats, and implementing secure network architecture.
A critical component of the SY0-701 exam—and modern cybersecurity practices overall—is understanding and mitigating piracy and unauthorized usage of digital assets. As the digital landscape continues to grow exponentially, so does the threat of piracy. From movies and music to proprietary software and intellectual property, the unauthorized use of content poses serious challenges to organizations across industries. Understanding the tools, technologies, and legal frameworks surrounding this issue is essential—not only for passing the CompTIA SY0-701 exam but also for building a secure digital future.
Definition of Piracy and Unauthorized Usage
Piracy refers to the illegal copying, distribution, or use of copyrighted materials without proper authorization from the owner. This includes downloading music or software without a license, using cracked versions of paid programs, or redistributing digital content that is meant to be protected.
Unauthorized usage, while similar, may extend beyond piracy and include any form of accessing, using, or modifying data without the proper credentials or permissions. This might be internal misuse of resources by employees or external actors exploiting vulnerabilities in a system.
Both piracy and unauthorized usage undermine the rights of content creators, compromise data security, and cause financial losses for organizations. In the context of cybersecurity, preventing and controlling such threats is paramount, which is why it is covered in-depth in the CompTIA SY0-701 certification.
Key Technologies and Methods Used to Control Illegal Usage
Combating piracy and unauthorized access involves a multi-faceted approach that integrates cutting-edge technologies and strategic methods. Below are some of the most effective tools and systems used:
1. Digital Rights Management (DRM)
DRM is a set of access control technologies designed to restrict the use of proprietary software and digital media. It ensures that only authorized users can access the content under specific conditions. For example, DRM might prevent a user from copying a song file or printing a confidential document.
-
DRM is widely used in the entertainment and publishing industries.
-
It includes features such as license restrictions, usage tracking, and file encryption.
In the SY0-701 exam, candidates must understand how DRM works, its applications, and the ethical concerns it may raise.
2. License Management Tools
License management is the process of controlling and documenting how software and digital products are used. These tools help ensure that organizations are in compliance with licensing agreements and prevent unauthorized installations or usage.
-
They monitor the number of users accessing a particular software.
-
They can disable software when a license is expired or misused.
-
Cloud-based license tracking systems are becoming increasingly popular.
From a cybersecurity perspective, effective license management prevents legal issues and ensures that systems are protected against vulnerabilities introduced through pirated or outdated software.
3. Access Control Mechanisms
Access control determines who is allowed to access or use resources in a computing environment. These mechanisms are foundational in preventing unauthorized usage and include:
-
Discretionary Access Control (DAC): Allows users to control access to their own data.
-
Mandatory Access Control (MAC): Access rights are regulated by a central authority.
-
Role-Based Access Control (RBAC): Users are granted access based on their role within an organization.
These models are part of the SY0-701 exam's focus on secure network architecture and identity management.
4. Encryption Techniques
Encryption is the process of converting data into a code to prevent unauthorized access. It plays a crucial role in protecting sensitive information, especially when it's transmitted or stored.
-
Symmetric encryption uses the same key for encryption and decryption.
-
Asymmetric encryption uses a public key for encryption and a private key for decryption.
Encryption ensures that even if data is accessed illegally, it remains unreadable to unauthorized users. Understanding these techniques is essential for anyone preparing for the CompTIA SY0-701 exam.
5. Anti-Piracy Software and Tools
There are specific anti-piracy tools that monitor, detect, and block unauthorized usage of software and digital content. These include:
-
Software license enforcement tools that validate installations.
-
Watermarking tools that trace unauthorized distribution.
-
Digital forensics tools used to investigate piracy incidents.
These tools are part of the broader endpoint and application security strategy required for comprehensive cybersecurity.
Legal Frameworks and Regulations
Piracy and unauthorized usage are not just technological issues—they are also legal offenses. Various laws and regulations exist globally to combat these crimes, and understanding them is crucial for IT professionals.
Some key regulations include:
-
Digital Millennium Copyright Act (DMCA) – U.S. legislation that protects digital copyright.
-
General Data Protection Regulation (GDPR) – Governs data privacy and security in the EU.
-
Computer Fraud and Abuse Act (CFAA) – U.S. federal statute that criminalizes unauthorized computer access.
The CompTIA SY0-701 exam includes legal and compliance domains, requiring candidates to be familiar with these frameworks and understand how they influence cybersecurity policies.
Cybersecurity Implications for Organizations
Piracy and unauthorized usage can have devastating consequences for businesses and institutions. These implications include:
-
Financial Losses: Pirated software or unauthorized access can result in lost revenue, fines, and penalties.
-
Reputational Damage: If a company is found using pirated content or fails to protect intellectual property, its reputation may suffer irreparably.
-
Increased Vulnerability: Pirated software often lacks security updates, making systems more susceptible to malware, ransomware, and other cyber threats.
-
Legal Liabilities: Organizations may face lawsuits or regulatory action for failing to protect digital assets or for unintentionally promoting piracy.
An organization's cybersecurity posture must include strong measures against illegal digital activity. This aspect is thoroughly evaluated in the SY0-701 certification.
CompTIA SY0-701 Exam Connection
The CompTIA SY0-701 exam bridges the gap between theory and practice in cybersecurity. It is structured to test knowledge in five primary domains:
-
General Security Concepts
-
Threats, Vulnerabilities, and Mitigations
-
Security Architecture
-
Security Operations
-
Security Program Management and Oversight
Issues of piracy and unauthorized access intersect all these areas:
-
Threats and vulnerabilities include risks from pirated software or unauthorized data access.
-
Mitigation strategies involve using DRM, encryption, and access control mechanisms.
-
Security operations include monitoring systems for signs of piracy and taking corrective actions.
-
Governance and compliance sections focus on legal frameworks like the DMCA and GDPR.
Successfully passing the SY0-701 exam means understanding how to apply anti-piracy methods in real-world environments.
How DumpsBoss Helps You Prepare
DumpsBoss is a premier online platform offering expertly curated SY0-701 exam dumps, practice questions, and preparation materials. Here's how DumpsBoss can help you master the concepts:
1. Real-World Scenarios and Questions
DumpsBoss provides updated practice exams with questions tailored to real-world situations—like identifying and mitigating software piracy—which are frequently tested in the SY0-701 exam.
2. Comprehensive Study Guides
Our detailed guides cover all domains of the exam, including license management, encryption, and DRM tools, helping you understand not just what to study but why each topic matters.
3. Expert-Verified Dumps
All practice questions are verified by certified cybersecurity experts to ensure accuracy and alignment with the latest CompTIA objectives.
4. Easy-to-Use Interface
Our platform is intuitive and mobile-friendly, letting you study anytime, anywhere—ideal for working professionals and students alike.
5. High Success Rate
Thousands of candidates have trusted DumpsBoss and passed the CompTIA Security+ SY0-701 exam on their first attempt. With our help, you can too.
Conclusion
In today's hyper-connected digital age, the fight against piracy and unauthorized usage is more important than ever. The CompTIA SY0-701 certification ensures that IT professionals are equipped to recognize these threats and respond with proven, effective strategies.
From understanding encryption and DRM to knowing the ins and outs of access controls and anti-piracy tools, candidates must be well-versed in a wide range of technologies and legal frameworks.
DumpsBoss stands out as a trusted partner on your certification journey—offering real-world practice, expert insights, and comprehensive materials tailored to your success.
Prepare with DumpsBoss, pass with confidence, and become a cybersecurity professional who can tackle piracy and protect the digital world.
Special Discount: Offer Valid For Limited Time “SY0-701 Exam” Order Now!
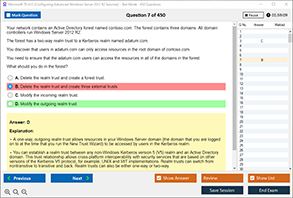
Sample Questions for CompTIA SY0-701 Dumps
Actual exam question from CompTIA SY0-701 Exam.
What is used to control the illegal use of software and digital content?
A) Firewall
B) Digital Rights Management (DRM)
C) Antivirus
D) Encryption