Overview of the CompTIA SY0-701 Exam
The CompTIA SY0-701 exam is the latest version of the globally recognized Security+ certification. It validates the foundational skills required to perform core security functions and pursue an IT security career.
Key domains covered in the SY0-701 exam include:
-
Threats, vulnerabilities, and attacks
-
Security architecture and design
-
Security operations
-
Incident response and recovery
-
Governance, risk, and compliance
On-Path Attacks are part of the threats and vulnerabilities domain, making it crucial for test-takers to grasp this concept in-depth. DumpsBoss provides updated SY0-701 dumps and practice tests to help candidates pass with confidence.
What is an On-Path Attack?
An On-Path Attack occurs when an attacker secretly intercepts and possibly alters the communication between two parties who believe they are directly communicating with each other. The attacker can eavesdrop, steal data, manipulate content, or inject malicious payloads without the parties knowing.
The term “On-Path” emphasizes the attacker’s position between two endpoints—be it through a compromised router, software vulnerability, or rogue network device.
Core Components of On-Path Attacks
To execute an On-Path Attack, an attacker needs:
-
Access to the Network: Either physical access or remote control of a device within the network.
-
Spoofing or Redirection Technique: Manipulating routing mechanisms like ARP or DNS to redirect traffic.
-
Packet Sniffing or Interception Tools: Tools like Wireshark or Bettercap that capture and analyze data.
-
Session Hijacking or Data Injection Ability: Capability to manipulate or steal ongoing sessions or insert malicious data.
Examples of On-Path Attacks
Let’s examine some common and real-world instances of On-Path Attacks:
ARP Spoofing / ARP Poisoning
ARP (Address Resolution Protocol) spoofing is a type of On-Path Attack in local area networks (LANs). The attacker sends forged ARP messages to associate their MAC address with the IP address of a legitimate device (like a router). This causes network traffic to flow through the attacker.
Impact: Allows data interception, session hijacking, and traffic manipulation.
Detection & Prevention:
-
Use static ARP entries
-
Enable Dynamic ARP Inspection (DAI)
-
Monitor network for abnormal ARP traffic
DNS Spoofing / DNS Poisoning
In DNS spoofing, an attacker corrupts the DNS cache of a server or system, redirecting a user to a malicious site instead of the intended legitimate one.
Example: A user enters sample.com, but the attacker redirects them to a fake phishing site that looks identical.
Defense Mechanisms:
-
Use DNSSEC (Domain Name System Security Extensions)
-
Implement DNS filtering solutions
-
Regularly flush DNS cache
SSL Stripping
SSL Stripping downgrades a user’s connection from HTTPS to HTTP, removing encryption. The attacker intercepts a secure HTTPS request, responds with HTTP, and forwards the request to the real server using HTTPS, acting as a middleman.
Result: The user believes they’re on a secure connection, but all data can be read and altered by the attacker.
Mitigation:
-
Implement HSTS (HTTP Strict Transport Security)
-
Use only secure public Wi-Fi
-
Employ browser plugins that force HTTPS
Session Hijacking
In this attack, the attacker captures or predicts a valid session token to gain unauthorized access to an active session.
Real-World Use Case: An attacker steals session cookies during login to access user accounts on banking platforms or email.
Countermeasures:
-
Use encrypted cookies and secure session tokens
-
Employ multi-factor authentication (MFA)
-
Enable session timeouts
Wi-Fi Eavesdropping with Rogue Access Points
Attackers set up rogue Wi-Fi hotspots with names resembling legitimate networks. Unsuspecting users connect, thinking it's safe, but all data transmitted is now exposed.
Tactics Used:
-
Evil Twin Attacks
-
Packet sniffing
-
Credential harvesting
Best Practices:
-
Educate users about connecting only to trusted networks
-
Use VPNs on public Wi-Fi
-
Implement wireless intrusion detection systems (WIDS)
Email Interception via SMTP Attacks
Email communications that aren’t properly secured via SSL/TLS encryption can be intercepted using SMTP (Simple Mail Transfer Protocol) attacks.
Threats Include:
-
Reading confidential emails
-
Injecting malicious links
-
Spoofing sender identities
Protection Methods:
-
Use end-to-end encryption (e.g., PGP)
-
Enable STARTTLS for SMTP
-
Authenticate email servers with SPF, DKIM, and DMARC
Tools Commonly Used in On-Path Attacks
Understanding the tools involved can help identify and stop on-path attacks. Here are some widely used tools by attackers:
-
Wireshark: Packet capturing and analysis
-
Ettercap: Conducts ARP poisoning and traffic sniffing
-
Bettercap: Advanced tool for network attacks, particularly ARP spoofing and DNS spoofing
-
Cain and Abel: Password recovery and sniffing tool for Windows
-
MITMf (Man-In-The-Middle Framework): Automates interception and modification of HTTP, HTTPS, and DNS traffic
-
Aircrack-ng: Used for wireless attacks, including sniffing WPA/WPA2 handshakes
Prevention and Mitigation Strategies
Defending against On-Path Attacks requires a layered security approach. Here are essential strategies:
1. Encryption Everywhere
-
Use HTTPS and enforce HSTS.
-
Implement end-to-end encryption for messaging and email.
2. Secure Network Architecture
-
Segment networks using VLANs.
-
Use strong router passwords and disable unused ports.
3. Authentication and Access Control
-
Implement MFA.
-
Use role-based access controls (RBAC).
4. Security Awareness Training
-
Teach users to identify phishing attempts and avoid untrusted networks.
-
Train staff to recognize unusual system behavior.
5. Monitoring and Intrusion Detection
-
Use tools like Snort or Suricata to detect abnormal traffic.
-
Set up alerts for ARP and DNS anomalies.
6. Patch Management
-
Regularly update routers, firewalls, and client software to patch known vulnerabilities.
Relevance to CompTIA SY0-701 Exam
Understanding On-Path Attacks is critical for success in the CompTIA SY0-701 Security+ exam. The exam tests your ability to:
-
Recognize and describe various types of cyberattacks
-
Analyze indicators of compromise (IoCs)
-
Implement countermeasures and security best practices
The DumpsBoss platform provides reliable and up-to-date SY0-701 dumps, practice questions, and expert study materials that include in-depth coverage of On-Path Attacks and related security concepts.
Using DumpsBoss resources, you can master the core content required to pass the exam and gain hands-on knowledge to tackle real-world cybersecurity challenges.
Conclusion
On-Path Attacks remain one of the most dangerous and prevalent cybersecurity threats. They allow attackers to intercept, manipulate, and exploit sensitive data by inserting themselves into a trusted communication channel. From ARP poisoning to SSL stripping and session hijacking, the techniques involved are sophisticated—but so are the defenses.
Preparing for the CompTIA SY0-701 Exam means going beyond memorization—you need to understand how these attacks work, how to detect them, and how to defend against them. With top-tier resources from DumpsBoss, you can ensure thorough preparation and exam readiness.
Whether you're a cybersecurity aspirant or an experienced IT professional, mastering the mechanics of On-Path Attacks will make you more effective in securing networks, protecting users, and responding to threats.
Ready to pass the SY0-701 exam? Trust DumpsBoss for expert-verified dumps, accurate practice tests, and exam-focused learning strategies.
Special Discount: Offer Valid For Limited Time “CompTIA SY0-701 Dumps” Order Now!
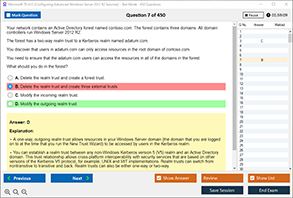
Sample Questions for CompTIA SY0-701 Exam Dumps
Actual exam question from CompTIA SY0-701 Exam.
Which of the following are examples of on-path attacks?
A) Man-in-the-Middle (MitM) and Man-in-the-Browser (MitB)
B) Phishing and Spear Phishing
C) SQL Injection and Cross-Site Scripting
D) Denial-of-Service and Brute Force