Overview of the CompTIA SY0-701 Exam
The CompTIA Security+ SY0-701 exam is a globally recognized certification designed for cybersecurity professionals aiming to validate their foundational knowledge in security practices and principles. As the threat landscape continues to evolve, organizations increasingly demand skilled professionals who can ensure the confidentiality, integrity, and availability of information. The SY0-701 exam evaluates a candidate’s ability to identify, analyze, and respond to security threats, as well as their understanding of security architecture, risk management, and secure system design.
One of the critical topics covered in the SY0-701 exam is remote access security. In today's dynamic work environment, secure remote access is vital for maintaining productivity while ensuring organizational data and resources remain protected. DumpsBoss offers candidates comprehensive resources, including study guides, real exam questions, and practice tests tailored to the SY0-701 exam, with a special focus on remote access and other core security domains.
Definition of Remote Access
Remote access refers to the ability of users to access a computer, network, or data from a distant location. This access allows employees to work from home, access files on a corporate network, or manage systems located in different geographic regions. While convenient and often necessary, remote access poses significant security risks if not properly managed.
CompTIA SY0-701 emphasizes the importance of secure remote access because cybercriminals frequently exploit vulnerabilities in remote access configurations. Understanding secure methods of implementation is essential for passing the exam and protecting organizational assets.
Secure Configuration Options for Remote Access
To ensure secure remote access, organizations must implement robust configuration options that minimize exposure to cyber threats. Common secure configuration options include:
-
Least Privilege Access: Users should be granted only the access necessary to perform their job functions.
-
Encryption: Data transmitted over remote connections must be encrypted to protect against interception.
-
Timeouts and Session Controls: Inactive sessions should be terminated after a specific period to reduce the risk of unauthorized access.
-
IP Whitelisting: Limiting access to specific IP addresses or geographic regions adds an extra layer of security.
-
Patch Management: Keeping systems up-to-date with the latest patches closes known vulnerabilities.
Understanding and applying these secure configurations is essential for success on the CompTIA SY0-701 exam.
Use of Virtual Private Network (VPN)
A Virtual Private Network (VPN) is one of the most common and effective tools for secure remote access. VPNs create encrypted tunnels between the user's device and the organization's network, ensuring that transmitted data remains confidential.
There are two main types of VPNs:
-
Remote Access VPN: Used by individual users to connect securely to a private network.
-
Site-to-Site VPN: Connects entire networks to each other over the internet.
VPN protocols such as IPsec, SSL/TLS, and L2TP are covered in the SY0-701 exam. DumpsBoss provides detailed explanations and practice questions that help candidates master VPN concepts and configurations.
Secure Shell (SSH) for Command Line Access
Secure Shell (SSH) is a cryptographic network protocol used to securely access remote servers over an unsecured network. SSH provides encrypted command-line access, making it ideal for system administrators who need to manage remote machines.
Key features of SSH include:
-
Encrypted Communication: Prevents eavesdropping and data theft.
-
Authentication Mechanisms: Supports passwords, public key authentication, and multi-factor authentication.
-
Port Forwarding: Allows secure access to services running on a remote machine.
The SY0-701 exam tests candidates on secure remote administration, including the use of SSH. DumpsBoss helps reinforce this knowledge with scenario-based questions and simulation labs.
Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) is a security mechanism that requires users to present two different authentication factors to verify their identity. These factors fall into three categories:
-
Something you know (password or PIN)
-
Something you have (smartphone or hardware token)
-
Something you are (biometrics such as fingerprint or facial recognition)
Implementing 2FA significantly enhances remote access security by adding a second layer of defense. It mitigates the risk posed by stolen or guessed passwords. The SY0-701 exam places a strong emphasis on multi-factor authentication (MFA), making this a crucial area of study for examinees. DumpsBoss provides real-world examples and practice quizzes to aid understanding.
Access Control Lists (ACLs) and Firewall Rules
Access Control Lists (ACLs) and firewall rules are fundamental components in controlling traffic to and from a network. They help restrict access to authorized users and services only.
-
ACLs: Define rules that allow or deny traffic based on criteria such as IP addresses, ports, and protocols.
-
Firewall Rules: Determine which traffic is permitted or blocked at various network boundaries.
Proper implementation of ACLs and firewalls is essential for minimizing the attack surface of a network. For the SY0-701 exam, candidates must understand how to configure and interpret ACLs and firewall rules. DumpsBoss provides comprehensive walkthroughs and mock exams that simulate these configurations.
Strong Password Policies
Strong password policies are a simple yet effective way to secure remote access. Passwords should be:
-
At least 12 characters long
-
Include uppercase and lowercase letters, numbers, and special characters
-
Avoid dictionary words and common phrases
-
Changed regularly
Additional measures include password history, minimum age, and complexity requirements. The SY0-701 exam evaluates a candidate’s knowledge of password policy best practices. DumpsBoss highlights key policy considerations and includes related questions in their exam prep materials.
Network Access Control (NAC)
Network Access Control (NAC) is a security approach that restricts access to a network based on compliance with predefined policies. NAC systems assess the posture of devices before allowing them onto the network.
Key features include:
-
Pre-admission Checks: Ensuring devices meet security standards before granting access
-
Post-admission Control: Continuously monitoring devices for policy compliance
-
Integration with Directory Services: Enabling role-based access
NAC plays a critical role in ensuring that only authorized and compliant devices can access network resources. DumpsBoss provides real-life use cases and test questions that help learners understand the implementation and management of NAC.
Best Practices for Secure Remote Access
Securing remote access requires a holistic approach that combines multiple strategies. Best practices include:
-
Use Encrypted Connections: Always use VPNs, SSH, or HTTPS to encrypt data in transit.
-
Apply the Principle of Least Privilege: Limit user access to only what is necessary.
-
Regularly Update Software: Patch vulnerabilities to prevent exploitation.
-
Monitor Remote Sessions: Use logging and auditing tools to detect unusual activity.
-
Educate Users: Provide training on secure remote access habits and threat awareness.
-
Implement Endpoint Security: Ensure devices have updated antivirus, firewall, and security configurations.
DumpsBoss integrates these best practices into their study guides, giving candidates a practical understanding that helps in both the exam and real-world scenarios.
Common Mistakes and How to Avoid Them
When configuring remote access, several common mistakes can lead to vulnerabilities:
-
Weak Passwords: Easily guessable passwords undermine even the strongest systems.
-
Avoidance: Enforce strong password policies and use password managers.
-
-
No Multi-Factor Authentication: Relying solely on passwords increases risk.
-
Avoidance: Implement 2FA or MFA for all remote access points.
-
-
Improper VPN Configuration: Misconfigured VPNs can expose data.
-
Avoidance: Use standardized configurations and test thoroughly.
-
-
Lack of Monitoring: Unmonitored systems may harbor undetected threats.
-
Avoidance: Set up logs and alert systems for remote access activity.
-
-
Ignoring Patch Management: Unpatched systems are prime targets.
-
Avoidance: Automate patch deployment and track updates.
-
Understanding these mistakes and their solutions is crucial for passing the SY0-701 exam. DumpsBoss provides insights and real-world case studies that illustrate these issues and teach how to address them.
Conclusion
Securing remote access is a cornerstone of modern cybersecurity and a key focus area in the CompTIA SY0-701 exam. With the increase in remote work, organizations must implement robust measures such as VPNs, SSH, 2FA, ACLs, strong passwords, and NAC to protect their assets.
For candidates preparing for the SY0-701 exam, mastering the intricacies of secure remote access is essential. DumpsBoss offers a powerful suite of resources—including exam dumps, practice tests, study guides, and expert insights—to help candidates thoroughly understand these topics and succeed on the exam. Whether you're an aspiring security professional or an IT veteran aiming for certification, DumpsBoss is your trusted partner for achieving success in the cybersecurity field.
Special Discount: Offer Valid For Limited Time “CompTIA SY0-701 Dumps” Order Now!
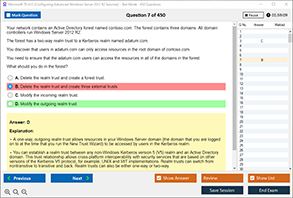
Sample Questions for CompTIA SY0-701 Exam Dumps
Actual exam question from CompTIA SY0-701 Exam.
What is a secure configuration option for remote access to a network device?
A) Telnet
B) FTP
C) SSH
D) HTTP