Overview of the CompTIA SY0-701 Exam
The CompTIA Security+ SY0-701 exam is a globally recognized certification for professionals seeking to demonstrate their expertise in the field of cybersecurity. It is designed for individuals who are responsible for managing the security of IT infrastructure and ensuring that their organization remains protected against a wide variety of cyber threats. This exam covers key areas, including network security, identity management, risk management, and the cryptographic techniques needed to secure sensitive data.
As businesses increasingly rely on digital infrastructures, securing these systems from unauthorized access has become paramount. One critical aspect of security is authentication—verifying the identity of users attempting to access systems or data. Authentication plays a central role in network security, and the CompTIA SY0-701 exam tests candidates' understanding of authentication methods, devices, and protocols. Mastering these concepts is essential for passing the exam and advancing in cybersecurity careers.
DumpsBoss offers an excellent array of study materials, including practice exams, study guides, and real exam dumps, specifically designed to help candidates pass the SY0-701 exam. By using DumpsBoss, individuals can familiarize themselves with the exam content, test their knowledge, and increase their chances of certification.
Types of User Authentication
User authentication is the process of verifying the identity of a user who is attempting to gain access to a system or network. It ensures that only authorized users can access sensitive data, applications, or systems. There are several methods of user authentication, each with its advantages and limitations. These methods are typically categorized into three main types: something the user knows, something the user has, and something the user is.
-
Something the User Knows
This is one of the most common forms of authentication and typically involves passwords or personal identification numbers (PINs). The user enters a secret piece of information to verify their identity. However, passwords and PINs can be vulnerable to attacks such as phishing, brute force, and social engineering. For this reason, they are often used in combination with other forms of authentication. -
Something the User Has
This method requires the user to possess a physical device that proves their identity. Examples include smart cards, hardware tokens, or smartphones that use one-time passwords (OTPs) or biometric data. This approach is more secure than traditional password-based authentication, as it requires the user to have a physical item in their possession. -
Something the User Is
Biometric authentication relies on unique physical traits of the user, such as fingerprints, facial recognition, retina scans, or voice recognition. This type of authentication offers a high level of security because biometric data is unique to each individual and difficult to replicate.
Additionally, some systems combine multiple authentication methods to provide multi-factor authentication (MFA), which significantly increases security by requiring users to prove their identity using more than one method.
The CompTIA SY0-701 exam covers these authentication methods and evaluates the candidate's ability to implement and manage authentication solutions effectively. Understanding the strengths and weaknesses of each method is crucial for passing the exam and ensuring robust security in real-world environments.
Devices for Verifying Identity on a Laptop
Laptops are commonly used in business and personal environments, and securing access to them is crucial to protect sensitive data and information. Authentication devices are essential for verifying a user’s identity when accessing a laptop. These devices come in various forms and are designed to strengthen security by implementing multifactor authentication techniques.
-
Smart Cards
A smart card is a physical device that contains a microprocessor and is used to authenticate a user. The user inserts the card into a card reader to gain access to the laptop. Smart cards are commonly used in enterprise environments and are typically paired with a PIN for added security. -
USB Security Tokens
USB tokens are small devices that plug into a USB port on the laptop. The device generates a one-time password (OTP) or holds a private key that is used for authentication. USB security tokens are portable and provide a high level of security, especially when combined with a PIN or password. -
Fingerprint Scanners
Fingerprint authentication is one of the most widely used biometric authentication methods. Laptops equipped with fingerprint scanners allow users to unlock their device with a simple swipe of their finger. This method is both convenient and secure, as fingerprints are unique to each individual. -
Facial Recognition
Facial recognition is a biometric authentication method that uses the laptop’s camera to scan and verify the user’s face. It compares the user’s facial features to those stored in a database. Many modern laptops, especially those running Windows 10 or later, come with facial recognition software built in, such as Windows Hello. -
Smartphone Authentication Apps
Many laptops now support authentication via smartphones. Apps like Google Authenticator, Microsoft Authenticator, or Duo Mobile generate OTPs or push notifications that the user can approve to gain access to the laptop. This method often works in combination with other forms of authentication, such as a password. -
Voice Recognition
Some laptops may use voice recognition technology to authenticate users based on their unique vocal patterns. While not as common as other authentication methods, voice recognition can provide a convenient hands-free way to unlock a laptop.
Each of these devices plays a critical role in securing access to laptops and ensuring that unauthorized users cannot gain entry. The right authentication device depends on the user’s needs and the level of security required.
Best Practices for Using Authentication Devices
While authentication devices significantly enhance laptop security, it is important to follow best practices to ensure that they remain effective and do not introduce vulnerabilities. Here are some key best practices for using authentication devices on laptops:
-
Use Multifactor Authentication (MFA)
One of the best ways to secure laptops is by implementing multifactor authentication. MFA requires users to provide multiple forms of authentication, such as a password and a fingerprint scan, making it much harder for unauthorized users to gain access. Combining authentication methods—such as something the user knows and something the user has—greatly increases security. -
Keep Authentication Devices Updated
Like any technology, authentication devices can have vulnerabilities that can be exploited by attackers. Regularly updating the software and firmware of authentication devices ensures that any security patches are applied promptly. This practice reduces the risk of security breaches. -
Secure Backup Authentication Methods
While it is essential to use strong primary authentication methods, it is equally important to have secure backup methods in place. If a user’s fingerprint scanner or smart card is lost or damaged, they should be able to securely authenticate through alternative means, such as a password or secondary device. -
Educate Users on Security Risks
Users should be educated about the risks of using weak or easily guessable authentication methods. For instance, using simple PIN codes or passwords that are easy to guess or hack can undermine the effectiveness of authentication devices. Encourage users to use strong, unique passwords or PINs and to avoid using the same authentication method for multiple systems. -
Use Trusted and Secure Devices
It is critical to use trusted and secure authentication devices. Only purchase devices from reputable manufacturers and vendors to ensure that they meet security standards and are free from vulnerabilities. -
Disable Default Authentication Settings
Many authentication devices come with default settings that are easy to bypass. Ensure that default passwords, PINs, and settings are disabled or changed during the initial setup of authentication devices. -
Physical Security of Authentication Devices
Devices such as smart cards and USB tokens should be physically secured when not in use. It’s important to ensure that these devices are stored in a safe place, away from potential theft or unauthorized access.
Real-World Examples of Authentication Devices Used in Laptops
Authentication devices are widely used in various real-world scenarios to protect sensitive data and ensure only authorized users gain access to laptops. Here are some real-world examples:
-
Government Agencies
Government agencies often use smart cards for employee authentication. These cards are used to access confidential data and ensure that only authorized personnel can access classified information. -
Enterprise Environments
In enterprise settings, employees often use fingerprint scanners or smart cards for logging into laptops and accessing corporate networks. This ensures that sensitive corporate data remains protected from unauthorized access. -
Educational Institutions
Many educational institutions use biometric authentication devices to protect access to student data and other critical information. Fingerprint scanners or facial recognition systems are often implemented to ensure security and convenience for students and staff. -
Healthcare Organizations
Healthcare professionals use authentication devices to protect patient information and comply with regulations such as HIPAA. Smart cards and fingerprint scanners are commonly used to access medical records and healthcare systems securely. -
Personal Devices
On a personal level, individuals often use fingerprint scanners or facial recognition technology to protect their laptops from unauthorized access. With the increasing threat of data breaches and cyberattacks, these devices help safeguard personal information from hackers.
Conclusion
Authentication is a critical component of cybersecurity, and the CompTIA SY0-701 exam assesses candidates’ knowledge of various authentication methods and devices. Understanding how to implement and manage authentication systems is essential for securing laptops and protecting sensitive data from unauthorized access.
DumpsBoss provides comprehensive study materials, practice exams, and real exam dumps designed to help individuals prepare effectively for the CompTIA SY0-701 exam. By leveraging these resources, candidates can gain a deep understanding of authentication concepts and increase their chances of passing the exam with confidence.
With the right knowledge of authentication devices, best practices, and real-world applications, IT professionals can enhance the security of their organizations and ensure that sensitive data remains protected from cyber threats.
Special Discount: Offer Valid For Limited Time “CompTIA SY0-701 Dumps” Order Now!
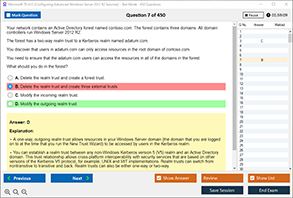
Sample Questions for CompTIA SY0-701 Exam Dumps
Actual exam question from CompTIA SY0-701 Exam.
Which type of device would be used on a laptop to verify the identity of a user?
A) Webcam
B) Fingerprint scanner
C) Mouse
D) External hard drive